When you visit a website, especially one where you’re entering sensitive info like passwords or credit card numbers, there’s an process called SSL handshake happening behind the scenes to keep your data safe. The handshake is like a digital handshake between your browser and the server, establishing a secure channel for data exchange. Without this key step, all information transmitted over the internet would be vulnerable to interception and tampering. So, understanding what an SSL handshake is and how it works can demystify the security processes that protect our online interactions.
Table of Contents
Understanding the SSL handshake: The foundation of secure connections
What is an SSL handshake and why does it matter?
An SSL handshake is a crucial initial step in creating a secure connection between your device (the client) and a web server. It’s essentially an agreement—both parties decide on encryption methods, authenticate identities, and generate session keys that will be used to encrypt subsequent communications. Think of it as a secret code negotiation where both sides confirm they are who they say they are and agree on how to communicate safely.
This process matters because it forms the backbone of HTTPS—the secure version of HTTP—and ensures that any data exchanged remains confidential and tamper-proof. When you see that padlock icon in your browser bar or notice “https://” at the start of a URL, it indicates that an SSL handshake has successfully taken place before any actual data transfer begins.
How SSL handshake ensures data security and privacy
The primary purpose of the SSL handshake is to establish trust and set up encryption parameters so that sensitive information stays private during transmission. During this process:
- The server presents its digital certificate—an electronic ID card issued by a Certificate Authority—that proves its identity.
- The client verifies this certificate to ensure it’s communicating with the legitimate website.
- Using asymmetric encryption techniques, both parties securely exchange cryptographic keys.
- A shared symmetric session key is generated, which encrypts all subsequent data exchanges efficiently.
By doing so, the SSL handshake guarantees that third parties cannot eavesdrop on or alter the data passing between your device and the server. It also confirms that both entities adhere to agreed-upon security standards—like supported TLS versions and cipher suites—making sure everyone’s on the same page for maximum protection.
The 5 Key Steps Behind the SSL handshake
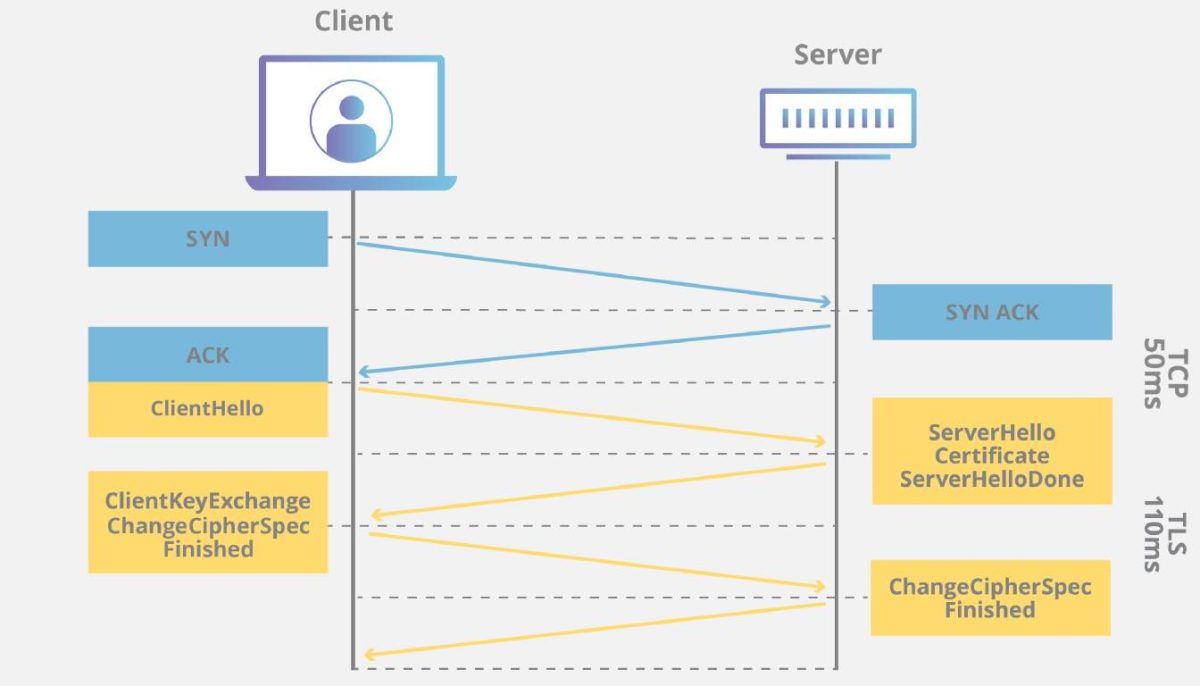
Breaking down this complex process into manageable steps helps clarify how two devices coordinate their security settings in milliseconds. Here are the core stages involved:
Step 1: Client Hello – Initiating the secure connection
It all begins when your browser sends a “ClientHello” message right after you request a secure webpage. This message includes:
- Supported SSL/TLS versions (like TLS 1.2 or 1.3)
- Cipher suites (sets of encryption algorithms) it can handle
- Randomly generated data known as “client random”
This initial hello acts like saying: “Hey! I want to talk securely; here’s what I support.”
Step 2: Server Hello – Choosing encryption parameters
The server responds with “ServerHello,” which contains:
- The highest SSL/TLS version both support
- Selected cipher suite from those offered by the client
- Another random number (“server random”)
This stage sets up common ground for encryption protocols both sides will use during their session.
Step 3: Certificate exchange and authentication
Next comes presenting digital credentials—the server sends its certificate containing its public key along with other identification details. This certificate is issued by trusted authorities called Certificate Authorities (CAs). Your browser then verifies this certificate against known CAs to confirm authenticity.
If mutual authentication is used (Mutual TLS), your device may also present its own certificate for verification by the server, adding an extra layer of trust.
Step 4: Key exchange and session key creation
Here’s where asymmetric encryption shines:
- Your browser uses the server’s public key from its certificate to encrypt a “premaster secret.”
- This encrypted premaster secret travels back to the server.
- The server decrypts it using its private key.
Both sides then independently generate identical session keys from this premaster secret combined with previous random values—these symmetric keys are fast-performing tools used for encrypting all further communication.
Step 5: Finalization and encrypted communication begins
Once both parties confirm they’ve received each other’s messages correctly—often through specific “Finished” messages—they switch over entirely to symmetric encryption using these session keys.
From this point onward, all data exchanged is encrypted symmetrically, ensuring confidentiality throughout your browsing session.
| Step | Description | Data Exchanged | Purpose |
|---|---|---|---|
| 1 | ClientHello | Supported protocols & cipher suites | Initiate connection & propose options |
| 2 | ServerHello | Chosen protocol & cipher suite | Agree on communication parameters |
| 3 | Server Certificate | Digital cert + public key | Authenticate server |
| 4 | Key Exchange Messages | Encrypted premaster secret & signatures | Establish shared session keys |
| 5 | Finished Messages & Switch Encryption Mode | Confirmation signals & switch-over commands | Confirm setup & begin encrypted transfer |
Common issues during the SSL handshake and troubleshooting tips
Despite its efficiency, problems can sometimes crop up during an SSL handshake, leading to errors like connection failures or warnings about untrusted certificates. Knowing how these issues manifest helps in resolving them quickly.
Identifying handshake failures and error messages
Common signs include error codes such as ERR_SSL_PROTOCOL_ERROR or ERR_CONNECTION_CLOSED in browsers. These often indicate mismatched protocol versions or invalid certificates blocking progress at various stages—be it during certificate verification or key exchange phases.
Monitoring network logs reveals details about failed handshakes—for example, if one side doesn’t support certain cipher suites or if there’s no common protocol version available between client and server.
Resolving certificate errors and mismatches
Certificate-related problems occur when browsers can’t verify a website’s identity due to expired certificates or untrusted CAs. To troubleshoot:
- Check if your device’s clock is accurate.
- Update browsers regularly.
- Ensure that websites have valid certificates issued by reputable authorities.
For site owners experiencing errors:
- Renew expired certificates promptly.
- Obtain certificates from trusted providers.
- Configure servers correctly with proper intermediate certificates.
Handling protocol version mismatches
Older protocols like SSL 2.0 or SSL 3.0 are deprecated due to security vulnerabilities; modern browsers block them automatically. If encountering such errors:
- Confirm that servers support recent TLS versions (preferably TLS 1.2/1.3).
- Disable outdated protocols in server configurations.
Ensuring compatibility across different systems involves updating software stacks so they favor current standards while avoiding insecure older versions.
Conclusion
SSL handshake is an important part of the secure communication process. It helps to ensure that the server and the client are both using the same security parameters and that the data being exchanged is encrypted and secure. Without SSL handshake, the data being exchanged between the server and the client could be intercepted and read by a third party. To ensure the security of your data, it is important to use an SSL certificate to enable SSL handshake.
If you are looking for a reliable SSL certificate provider, eSSL is the perfect choice. eSSL provides a wide range of SSL certificates to suit your needs. With eSSL, you can be sure that your data is secure and that your customers can trust your website. So, what are you waiting for? Buy SSL Certificate from eSSL today and secure your website!
For more detailed insights into securing web connections through robust cryptography, check out source.
Frequently asked questions on SSL handshake
What is the purpose of an SSL handshake?
The primary purpose of an SSL handshake is to establish a secure and trusted connection between your browser and the web server. During this process, they agree on encryption methods, verify identities using digital certificates, and generate session keys that encrypt all subsequent data exchanges. This ensures that your information remains private and protected from eavesdroppers.
How does the SSL handshake ensure data security?
The SSL handshake guarantees data security by authenticating both parties with digital certificates, exchanging cryptographic keys securely through asymmetric encryption, and then switching to faster symmetric encryption for the actual data transfer. This layered approach keeps sensitive info like passwords or credit card numbers safe during online transactions.
What are the main steps involved in an SSL handshake?
The SSL handshake involves five key steps: Client Hello, Server Hello, certificate exchange and authentication, key exchange and session key creation, followed by finalization where encrypted communication begins. Each step builds upon the previous one to create a secure channel in milliseconds.
Why do SSL handshakes sometimes fail?
SSL handshake failures can happen due to issues like incompatible protocol versions, invalid or expired certificates, or unsupported cipher suites. Common error messages include ERR_SSL_PROTOCOL_ERROR or certificate warnings. Troubleshooting often involves checking server configurations, updating certificates, or ensuring software supports current TLS standards.
What happens during an SSL handshake?
The SSL handshake involves exchanging supported protocols and cipher suites, verifying server identity with digital certificates, securely exchanging cryptographic keys, and finally establishing encrypted communication for your browsing session.
How long does an SSL handshake take?
An SSL handshake typically occurs within milliseconds—almost instantaneously—so users usually don’t notice it happening behind the scenes when accessing secure websites.
Can SSL handshakes be intercepted?
If not properly implemented or if there are vulnerabilities in older protocols like SSL 2.0 or 3.0, SSL handshakes could potentially be intercepted by malicious actors. That’s why modern TLS versions are crucial for maintaining security during these processes.
Is the SSL handshake different from TLS?
The term SSL handshake is often used interchangeably with TLS handshakes since TLS (Transport Layer Security) is its successor. Modern secure connections primarily rely on TLS protocols which follow similar steps but offer improved security features.
